 By Jake Anderson
By Jake Anderson
Sometimes conspiracy theories turn out to be true. Therefore, it’s worth assessing them, even if their claims appear wholly outlandish. Especially if their claims appear wholly outlandish.
Generally speaking, conspiracy theories form where there is a vacuum of verifiable facts associated with a controversial, usually tragic event. The concept has evolved over the years and is a part of our popular culture.
There are legions of conspiracy theorists and “truthers” who have devoted their lives to certain theories, and there are legions of skeptics who have devoted their lives to debunking those theories. All the while, conspiracy theories of every stripe and variety festoon the footnotes of history. Even the origin of the phrase itself is subject to conspiracy theory, as some researchers have argued that the CIA invented and promulgated the term in order to marginalize fringe thinkers and neutralize investigations.
The internet has obviously had a profound effect on conspiracy theories, simultaneously helping and hurting the cause. While a world of information is at people’s fingertips, so to are alternate worlds of manufactured propaganda. While the Internet may appear to be a democratized, unfiltered path toward facts and truth, it is easily manipulated. Powerful corporations pay a lot of money to have their dirty laundry buried in the search results underneath contrived puff pieces.
With nearly the entire mainstream media apparatus at their disposal, the government is a maestro at this practice. As we learned from so-called Operation Mockingbird — a conspiracy theory fact discussed in my first post on the subject, “Conspiracy Theories That Turned Out to Be True,” — hundreds, if not thousands of news organizations have been conscripted into working with the CIA to support pro-government narratives. That was in the 1960s. One can only imagine how vast the network is now. Not to mention the fact that a single proprietary algorithm owned by Google dictates the vast majority of the population’s exposure to a subject.
In Part 1, I noted that the list had been meticulously whittled down to focus only on conspiracies that have been irrefutably proven to be fact. There are hundreds of conspiracy theories I think are likely to be true that are not on this list because there simply isn’t enough hard evidence yet to confirm it 100%. I also aimed for a good mixture of old conspiracies and new conspiracies. With groups like Wikileaks and Anonymous out there, the last decade has witnessed a dam burst of new data and documents. Thanks to intrepid journalists, whistleblowers, hacktivists, and leakers, the human race continues to tear down the wall of lies erected by the corporatocracy.
Without further ado, let’s get to it….ten more conspiracy theories we can start calling conspiracy facts.
1. Operation Ajax, the CIA’s Iranian Coup

In Iran it was called 28 Mordad coup; the United Kingdom contributed under the name Operation Boot. However you refer to it, Operation Ajax was an Iranian coup that in 1953 deposed the democratically elected Muhammad Mossadeq and reinstalled the monarchical power of Shah Mohammed Reza Pahlavi. The primary cause of the coup was Mossadeq’s attempt to nationalize the Iran’s oil fields, which threatened the oil profits of Britain’s Anglo-Persian Oil Company (AIOC). The U.S. — in addition to protecting its ally’s petroleum monopoly — viewed Mossadeq’s move as communist aggression and therefore helped plan the return to power of one the world’s more insidious dictators, the shah. Operation Ajax resulted almost directly in 1979 Iranian revolution that created an anti-West Islamic republic led by the Ayatollah Khomeini.
Though it was long considered an open secret, the U.S. government kept the truth behind Operation Ajax concealed from the American people until very recently. The CIA declassified various documents on the 60th anniversary of the coup.
Because of the recent declassification, much information relevant to this CIA-sponsored coup is now available in the CIA’s archives.
In describing Operation Ajax, the CIA itself has become rather oddly self-reflective:
“The world has paid a heavy price for the lack of democracy in most of the Middle East. Operation Ajax taught tyrants and aspiring tyrants that the world’s most powerful governments were willing to tolerate limitless oppression as long as oppressive regimes were friendly to the West and to Western oil companies. That helped tilt the political balance in a vast region away from freedom and toward dictatorship.”
In a recent interview on Democracy Now, Bernie Sanders remarked to Amy Goodman that this seminal chapter in the history of U.S./Middle East relations is almost entirely ignored by mainstream media. “Have you seen many shows about that on NBC?” he asked the crowd.
2. “Nayirah,” the False Pretext for the first Gulf War
It’s now commonly believed that the second Iraq War was sold to the American people — and their congressional representatives — based on an elaborate web of lies and manipulated intelligence. What is less commonly known is that the first Iraq War came about in a very similar fashion. While, surprisingly, there is broad agreement that “Operation Desert Storm” was a worthwhile war, many people overlook the role of a fifteen-year-old girl named “Nayirah,” whose 1990 testimony to the Congressional Human Rights Caucus is credited with cementing the idea of Iraqi war crimes in the American popular consciousness. Nayirah testified to having witnessed Iraqi troops tearing babies from their incubators in Kuwaiti hospitals and leaving them to die on the floor. It’s a profoundly disturbing image….and one that was entirely fictitious.
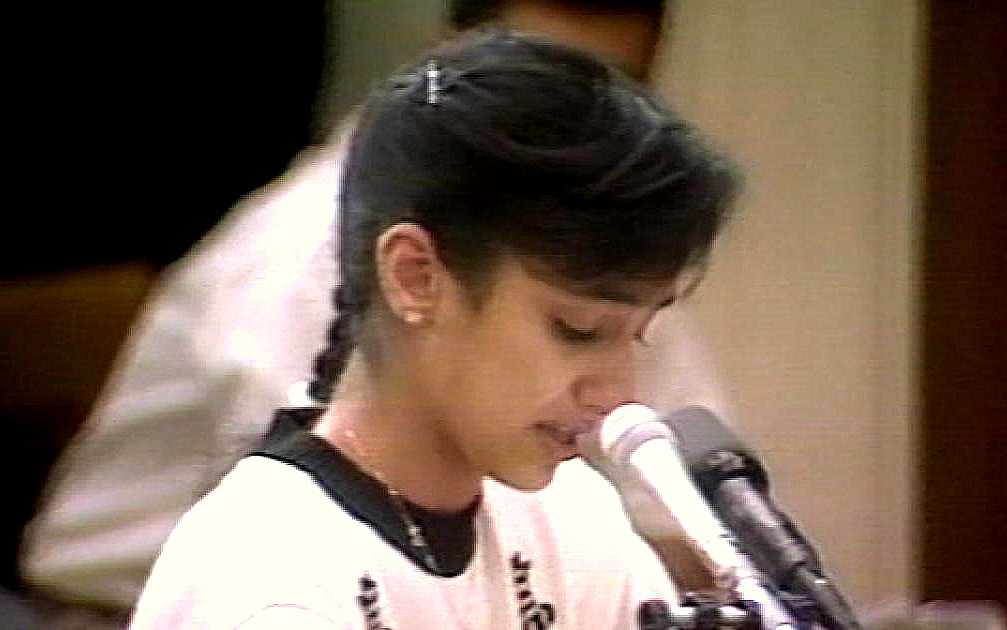
After a lengthy investigation, Amnesty International and other independent watchdog groups discovered that the situation described by Nayirah was fabricated by a PR firm named Hill & Knowlton (the largest in the world at this time), which was hired by the group Citizens for a Free Kuwait in order to create propaganda that would galvanize pro-war sentiment. The man overseeing the campaign was Bush political confidante Craig Fuller. This was a massive project utilizing 119 H&K executives in 12 offices across the United States and even involved casting Nayirah, who turned out to be Nayirah al-Sabah, daughter of Saud bin Nasir Al-Sabah, Kuwaiti ambassador to the United States. The Justice Department, which could have investigated the entire effort under the Foreign Agents Registration Act, turned a blind eye, allowing the Bush administration to pull off a massive “Wag the Dog”-style ideological false flag. Others call it “atrocity propaganda,” a form of psyop (psychological operation).
The “Nayirah” story is just another example of the government falsifying a narrative in order to manipulate the public into supporting war. This kind of psychological propaganda continued all through the second Iraq War and the War on Terror. Just recently, it was revealed that the Pentagon paid PR firm Bell Pottinger $540 million to create fake terrorist videos in Iraq.
3. Operation Paperclip
Originally called Operation Overcast, Operation Paperclip was the codename of the secret American plan to conscript Nazi scientists into U.S. intelligence services at the end of World War II. This ushered in and shielded about 1,500 Germans, including some engineers and technicians. Ostensibly, the purpose of this redeployment by the Joint Intelligence Objectives Agency (JIOA) was to prevent Nazi scientific intelligence from helping reconstitute a new German government; it was also a tactic meant to ensure the Soviet Union didn’t acquire any new technology.
Whatever strategic mindset might have lived inside Operation Paperclip, at its core, the project gave American identities to some of the most ruthless war criminals the world has ever seen.
According to Ynet, the new Nazi CIA scientists helped develop chemical weapons for the U.S. and worked alongside American scientists to develop LSD, which the CIA viewed as a ‘truth serum.’
4. Operation Gladio: Anti-Communist False Flags in Italy
Operation Gladio was the post-World War II love-child of a CIA/NATO/M16 plot to battle communism in Italy. The operation lasted two decades and used CIA-created “stay behind” networks as part of a “Strategy of Tension” that coordinated multiple terrorist attacks from the late 1960s to the early 1980s. Authorities blamed these attacks on Marxists and other left-wing political opponents in order to stigmatize and condemn communism. The operation involved multiple bombings that killed hundreds of innocent people, including children. The most notable attack was the August 2, 1980, bombing of the Bologna train station, which killed 85 people.
In an Anti-Media piece written about five confirmed false flag operations (which includes Operation Gladio, I wrote:
“How do we know about Operation Gladio in spite of its incredibly clandestine nature? There are two principle sources. One, the investigations of Italian judge Felice Casson, whose presentation was so compelling it forced Italian Prime Minister Giulio Andreotti to confirm Gladio’s existence. The second source is testimony from an actual Gladio operative, Vincenzo Vinciguerra, who is serving a life sentence for murder. In a 1990 interview with the Guardian, Vincenzo stated that Gladio was designed to psychologically coerce the Italian public to rely on the state for security.”
Operation Gladio is a textbook modern “false flag.” It used terror and violence to discredit an ideology (communism). And to think, this came at a time before the internet when the CIA didn’t have a fully entrenched mainstream media to trumpet, echo, and build consensus around every little nuance (though they were working on it with COINTELPRO and Operation Mockingbird). Nowadays, the CIA has multinational propaganda machines — the news networks — to make sure all terrorist attacks fit into the carefully scripted narrative that manufactures consent around our wars for oil, natural gas, and other resources.
5. Government uses insect and rodent drones to spy
It’s somewhat of a cliche to jokingly refer to a surrounding insect or bird as a clandestine spy deployed by the government to watch you. While we lack certain specifics on the ubiquity of the technology, we know definitively that the government has the technology to surveil citizens using insects and other small animals, and they use this technology in military applications.
There is some evidence to suggest that insect drones are used domestically to spy on citizens. In 2007, this theory conspiracy theory took shape when anti-war protesters reported strange buzzing insects. Written off as tin foil material, officials dismissed the suggestion that the government used insect drones to spy. Multiple witnesses reported erratic dragonfly-type objects hovering in the sky. The very next year, the U.S. Air Force announced their intended use of insect-sized spies ‘as tiny as bumblebees’ to infiltrate buildings in order to ‘photograph, record, and even attack insurgents and terrorists.‘ The government has come clean about its use of drones to spy on American citizens, so it’s difficult to believe they wouldn’t have at least tried insect drones.
While we can’t say with 100% certainty that there are insect drones spying on American citizens, though it’s exceedingly likely, what is irrefutable is the use of micro air vehicles (MAVs) and “spy animals” as war-time tools. DARPA launched its Stealthy Insect Sensor Project in 1999 as an effort to deputize bees as bomb locators in war zones. This was just the first phase in an ongoing project. In her book The Pentagon’s Brain: An Uncensored History of DARPA, America’s Top Secret Military Research Agency, journalist Annie Jacobsen revealed that the agency’s near-future trajectory is to introduce “biohybrids” — part animal, part machine cyborgs — into the United States’ military arsenal.
In an interview with Coast to Coast AM, Jacobsen said:
“DARPA has already succeeded in creating a rat that will be steered by remote control by implanting an electrode in its brain.
“And it’s done the same thing with a moth which is really remarkable because the scientists implanted the electrodes in the pupa stage of the moth when it was still a worm! And then it transformed into having wings, and those tiny little micro-sensors transformed with the moth and the DARPA scientists were able to steer that moth.”
This section references information from The Pentagon’s Brain: An Uncensored History of DARPA, America’s Top Secret Military Research Agency by Annie Jacobsen. Details not linked to external sources are cited in this book.
6. CIA assassinations and coups in foreign countries
When operatives for the Democratic Party claim the 2016 United States presidential election was tampered with by a foreign entity, it’s hard not to cringe at the irony. Firstly, they’ve presented no evidence, except to claim that government intelligence agencies believe it to be true. Sorry, that’s not actually evidence. That’s like the police saying they have DNA evidence but never actually scientifically presenting it in court. It’s kind of unnerving that we even have to point that out. Secondly, our own government and intelligence agencies, namely the CIA, have actively and aggressively subverted countless foreign elections over the last century and, in some cases, have outright funded the assassinations of candidates.
This subject could easily fill a multi-volume book, and countless authors have worked over the years to uncover the role of the CIA in foreign coups. Using every tool in their arsenal — including white, grey, and black psychological operations, counterinsurgencies, and brutal coups aimed at repressing and destroying radically democratic candidates — the CIA has subverted the “will of the people” across the world.
The most commonly noted instances of the CIA meddling in foreign elections and governments include the following:
This is but a small sampling of countries where even mainstream news outlets and, in many cases, the CIA itself, admits calamitous U.S. involvement. There are literally dozens more and, of course, this is restricting the conversation to soft coups — otherwise, we could certainly include the complete military decimation of Iraq, Afghanistan, Libya, and other Middle Eastern countries during the War on Terror, as well as the myriad imperial wars against perceived communist threats.
‘A foreign government hacked and subverted our election!’
The irony is thick with this one. Payback’s a bitch…..which, of course, isn’t giving our intelligence agencies, who have proven themselves to be pathological liars, the benefit of the doubt regarding their claims of Russian collusion during the 2016 presidential election. It’s just to kind of say…..you reap the harvest you have sown. When you look at the track record of the United States government, it’s a wonder the average citizen is safe traveling abroad.
7. Mainstream media is the propaganda branch of the State Department

People have long accused the media of being a proxy branch of the State Department, a highly sophisticated and well-produced form of manufactured consensus and controlled opposition all rolled into one. In ostensibly democratic nations, a free and independent press is of paramount importance. But in the U.S., we find a cohesion of the state and corporate news networks that do not constitute ‘state-run media’ in the traditional sense — but it’s close.
Our first solid documentation that the media is an echo chamber for the government came with the disclosure of what has come to be called Operation Mockingbird. This nefarious and far-reaching conspiracy was documented in Part 1 and involved the CIA essentially conscripting journalists, American news agencies, and major broadcasters to become domestic propagandists and spies. Eventually, this CIA/media symbiosis included journalists from all the top news organizations. Literally, thousands of people were involved.
This infiltration of the American media and press took place during the 1950s, at the start of the Cold War, and was carried out under the auspices of fighting communism. The CIA began to restrict its use of journalists in the Operation Mockingbird program in 1976, but many people believe it has since transmogrified into something far more powerful, nefarious, and ubiquitous today. We’re still in the early stages of proving to the masses that mainstream media is little more than a mouthpiece and propaganda machine for the government and its various agencies, but the evidence is accumulating.
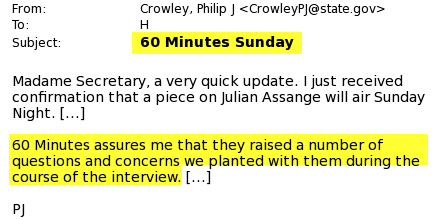
During the 2016 presidential election, Wikileaks exposed a number of disturbing revelations showing collusion between the media and political operatives. This included collusion between the media, the Democratic National Committee, and the Hillary Clinton campaign. But it wasn’t just about swaying the election. New revelations showed that the government actively infiltrates powerful media corporations in order to shape their content and narratives. One of the best examples of this was the State Department’s role in affecting a CBS 60 Minutes interview with Julian Assange.
A more comprehensive list of examples of the Orwellian symbiotic relationship between the press and the government can be found here.
Perhaps the most disturbing recent addition to this chapter was the “Countering Disinformation Act” that President Obama slipped into the National Defense Authorization Act (NDAA) on Christmas Eve of last year. In the context of the still-festering narrative of foreign interference in the 2016 presidential election, the act’s putative goal was to fight “fake news,” which many believe is actually a campaign to silence and dismantle alternative media on the Internet.
In order to accomplish this, the government is establishing a Global Engagement Center for managing disinformation and propaganda. Since we already know our government routinely performs psychological operations (psyops, or as they’ve been recently rebranded, Military Information Support Operations [MISO]), it should come as no surprise that manipulating the civilian population is a permanent goal. In fact, in the 2013 National Defense Authorization Act, the government formally legalized the use of psyops on U.S. citizens. So how does this Global Engagement Center factor in?
The new law states:
“The Center is authorized to provide grants or contracts of financial support to civil society groups, media content providers, nongovernmental organizations, federally funded research and development centers, private companies, or academic institutions for the following purposes:
To support local independent media who are best placed to refute foreign disinformation and manipulation in their own communities.
To collect and store examples in print, online, and social media, disinformation, misinformation, and propaganda directed at the United States and its allies and partners.
To analyze and report on tactics, techniques, and procedures of foreign information warfare with respect to disinformation, misinformation, and propaganda.
To support efforts by the Center to counter efforts by foreign entities to use disinformation, misinformation, and propaganda to influence the policies and social and political stability of the United States and United States allies and partner nations.”
While it may not immediately strike one as sinister, this codification of repressing journalists and voices the government deems to be disinformation while creating an even more centralized infrastructure to control “fact-based narratives” in the media should be highly alarming to anyone who cares about a free press. It would seem that while the State already has a steel grip on corporate news networks, they are struggling to control the influence of online independent media. This new law may be the start of this century’s Operation Mockingbird — a new full-scale infiltration of the local news and a war against anti-establishment narratives on the Internet. This is already taking the form of algorithmic censorship through Facebook and Google, as well as a weaponization of the “fake news” narrative.
8. The Deep State (or the conspiracy theory formerly known as The New World Order)
I describe the Deep State in depth in an article entitled “Forget the New World Order — Here’s Who Really Runs the World.” In it I wrote:
“For decades, extreme ideologies on both the left and the right have clashed over the conspiratorial concept of a shadowy secret government often called the New World Order pulling the strings on the world’s heads of state and captains of industry.
“The phrase New World Order is largely derided as a sophomoric conspiracy theory entertained by minds that lack the sophistication necessary to understand the nuances of geopolitics. But it turns out the core idea — one of deep and overarching collusion between Wall Street and government with a globalist agenda — is operational in what a number of insiders call the “Deep State.”
In the wake of the 2016 election, the concept of the Deep State has grown into somewhat of a common phrase in the lexicon of alternative media theorists, crossing political boundaries and resonating across the ideological spectrum. Everyone from alt-left socialists to alt-righters now agrees there is an unelected cabal of elite neo-conservative corporatists and crony lawmakers running the geopolitical show.
Because it’s such a complex subject and permeates so many different academic, economic, and state apparatuses, it’s virtually impossible to issue a single, simple definition of the Deep State. If I were to hazard one, I would call it “the nexus of Wall Street and the national security state — a relationship where elected and unelected figures join forces to consolidate power and serve vested interests.” But even that is vague. We could also call it “the failure of our visible constitutional government and the cross-fertilization of corporatism with the globalist war on terror.”
Former Republican congressional aide Mike Lofgren gets more specific with who is involved:
“It is a hybrid of national security and law enforcement agencies: the Department of Defense, the Department of State, the Department of Homeland Security, the Central Intelligence Agency and the Justice Department. I also include the Department of the Treasury because of its jurisdiction over financial flows, its enforcement of international sanctions and its organic symbiosis with Wall Street.”
In his writing, Lofgren emphasized the role of FISA international surveillance courts. This was confirmed in a very interesting way when President Donald Trump accused former President Obama of tapping his phones, a charge Obama aides deflected by saying that if such a warrant had been issued, it would have been done through a FISA court. This shows how presidents are able to skirt the constitution by outsourcing surveillance requests. It also shows the interconnectedness of these agencies.
However you want to describe it, it’s the natural conclusion of Operation Mockingbird and most certainly a reality that the elites would have rather kept under the radar. Fortunately for the people of the Earth, revelations from Wikileaks and other whistleblowers have, over the last couple decades, made it abundantly clear that the Deep State (the New World Order) not only exists, but also that it’s far more sinister and powerful than early conspiracy theorists could have ever imagined.
9. CIA used psychics to infiltrate the Soviet Union during Cold War
It’s a plot in a science fiction movie or TV show we’ve all seen: a psychic being leveraged by a law enforcement agency to track down a criminal. The concept of a government psychic program was popularized by the film The Men Who Stare at Goats, which lampooned the mythical STARGATE program supposedly run by the CIA. Most people scoffed at the reality of this and considered it a wacky conspiracy theory, but a recently declassified trove of hundreds of thousands of CIA files finally confirmed not only that psychics are regularly used by police and other law enforcement agencies, but also that the government actually weaponized psychics during the Cold War to try to infiltrate the Soviet Union and gain information.
The documents, made publicly available thanks to the activist group Muckrock, confirm there were top-secret CIA and Defense Department programs to use remote viewing to infiltrate Soviet military installments. There were also programs developing ways to engage in “psychic warfare,” including the development of a “psychic shield” to block Soviet psychics.
10. CIA monitors U.S. citizens via their smart devices

Early in 2017, the organization Wikileaks began releasing their first post-2016 election cables with a series of explosive data dumps regarding the CIA’s cyber hacking abilities and exploits. It is called Vault 7. Updated serially in “Year Zero,” “Dark Matter,” “Marble,” “Grasshopper,” “HIVE,” “Weeping Angel,” and “Scribbles,” the documents show the unprecedented collection of cyber vulnerabilities, exploits, and hacking abilities consolidated within the agency that many believe constitute wide-ranging breaches of civil liberties.
Chief among these breaches is domestic surveillance and extrajudicial cyberhacking, which the Wikileaks documents confirm are taking place in an abundance of forms. The Vault 7 documents confirm that: The CIA can break into Android and iPhone handsets and all kinds of computers; the agency has the ability to hack into Apple iPhones and Android smartphones and actually assume full remote control of the device; the CIA can access consumer smart TVs to listen in on surrounding conversations; the agency looked into ways to hack into cars and crash them, allowing ‘nearly undetectable assassinations’ (an assertion that may be relevant to the Michael Hastings case); the CIA concealed vulnerabilities that could be exploited by hackers from other countries or governments.
This is just the beginning. Early in the release, Julian Assange said the documents released represented only a tiny fraction of the total data that was forthcoming. Wikileaks’ episodic data dumps on the CIA’s cyber hacking programs are nothing less than stunning. The establishment’s reaction to the ongoing releases verifies how big of a deal they are. One congressman went so far as to refer to Julian Assange and his whistleblowing outfit as a “foreign terrorist organization.” This isn’t new or unexpected, as the group’s slow but inexorable drips of revelations about government malfeasance continue to confound and disturb private citizens, consumer rights activists, tech companies, and international leaders alike.
Reality Check
Of course, not all conspiracy theories are true. In fact, there are hundreds, even thousands, that have been roundly debunked. Unfortunately, there are those who seek to lie and invent fictions for monetary gain and fame. Misinformation, propaganda, and dishonesty exist at all levels of society.
However, sometimes conspiracy theories turn out to be true. Therefore, it’s worth assessing them, even if their claims appear wholly outlandish. Especially if their claims appear wholly outlandish.
The conspiracy theory is a tool in a larger toolkit used by those who wish to decode the grossly imperfect and fluid narrative describing our world. When investigated responsibly, conspiracy theories function as part of a conceptual spectrum of analysis with which we can investigate government and corporate abuses of power and the manufacturing of ‘consensus reality.’ In the 21st century, when the very transmission of information can be considered criminal, being a responsible conspiracy theorist just means you practice due diligence and hunger for the truth.
Source: Mint Press News



 By Ben Norton
By Ben Norton
 By Jake Anderson
By Jake Anderson
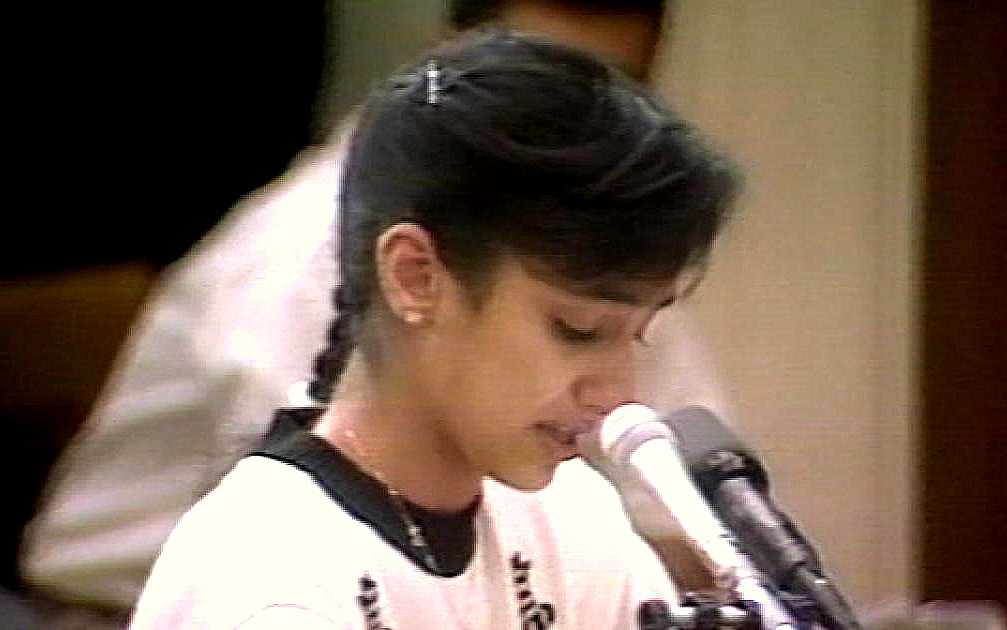



 By Olivia Solon
By Olivia Solon







